The Division of Protection has introduced a main new exertion to publish protection requirements and ideal tactics for govt DevSecOps and potentially company IT as perfectly, SearchITOperations has uncovered.
The exertion is led by Nicolas Chaillan, chief application officer for the U.S. Air Drive, and co-guide for the Company DevSecOps Initiative in the office environment of the Division of Protection (DoD) CIO. Chaillan said he has invited extra than two dozen organizations and open source entities to participate in 7 subgroups in Pest Control Surrey just the undertaking, which includes Microsoft, Purple Hat, VMware, StackRox, Pivotal, D2iQ, The Linux Foundation, The Cloud Indigenous Computing Foundation, Sysdig, Rancher and Splunk.
“[The Division of Protection] ordinarily has a unique approach, exactly where, for illustration, Purple Hat can build protection direction for RHEL or OpenShift — it can be ordinarily 1 business, 1 product,” Chaillan said. “This will be the whole Kubernetes ecosystem and community — all the Kubernetes distros, distributors and cloud providers we function with.”
The Cloud Indigenous Computing Foundation, StackRox, Sysdig and Rancher verified this week that they are participating in the undertaking, which has not been publicly declared prior to this report and as of yet, has no formal name. Other organizations Chaillan cited could not promptly be reached for comment.
National Institute of Criteria and Technological know-how (NIST) fellow Ronald S. Ross is also participating as a co-guide with Chaillan, with ideas to include DevSecOps direction to existing NIST SP 800-a hundred and sixty devices protection engineering requirements, and to publish new volumes that set up a DevSecOps reference architecture.
NIST and the DoD doing work team will collaborate on ideal tactics and protection requirements paperwork, with the objective of creating an early draft in just sixty to seventy five days, Chaillan said. The team will use a Git repository to edit and sustain the paperwork, which will be publicly obtainable.
NIST has a long heritage of doing work with community and private sector companies to set up protection requirements, but what tends to make this exertion special is the aim on making use of protection requirements to a certain use situation in DevSecOps, NIST’s Ross said.
“In the old days, the military and its contractors constructed devices that were only employed for military programs, which gave them a guide in excess of adversaries who didn’t have the exact same technologies,” Ross said. “But there has been a technologies explosion exactly where most devices are dual-use, created for both govt and commercial use — and adversaries have the exact same technologies.”
To safeguard the country, the DoD must set up a guide in the use of cloud-native systems and discover how to keep in advance of adversaries with ideal tactics, relatively than an absolute specialized edge, Ross said.
“This is the most important undertaking I have been included with in extra than thirty several years in the area of cybersecurity,” he included.
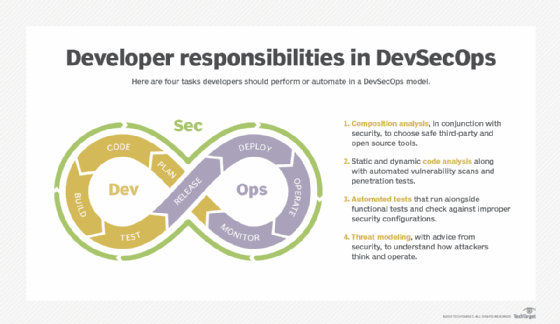
A potential DevSecOps template for enterprises
As govt companies and private-sector enterprises progressively use the exact same open source systems, many commercial organizations search to the govt, specially the DoD, as the gold conventional for cybersecurity, 1 IT consultant said.
“There’s a expressing, ‘Nobody at any time obtained fired for working with IBM,'” said Jeremy Pullen, principal specialized consultant at Polodis, a digital transformation consulting agency in Atlanta, who’s carefully next the DoD’s DevSecOps function, which includes a lately printed repository of hardened container images for normal use. “There’s a related assurance in working with devices hardened to the requirements of the US govt.”
Pullen said the breadth of the collaboration will also assistance legitimize the DevSecOps principle as a established of tactics, relatively than tying it to any unique device, vendor or approach employed by certain family-name company IT teams.
“The very last two several years, I have had to educate persons about what DevSecOps is and is just not — it can be not just working with a device from White Hat, Sonatype or Veracode,” he said. “This paints a far better image of DevSecOps as an location of follow relatively than just implementing somebody’s product.”
The exertion will also assistance the govt extra quickly procure new systems, which could translate into company procurement strategies, Pullen said.
This undertaking demonstrates a change in the federal government’s solution to tech, as perfectly as a normal change towards open source application, and open source knowledge sharing, throughout the IT business, said Shannon Williams, co-founder and president of Rancher, whose federal group will function on Kubernetes protection requirements.
Other open requirements, these kinds of as Heart for Net Safety (CIS) benchmarks, by now exist for this reason, but this undertaking will increase how they are joined to other DevSecOps applications and refine how protected application is created, Williams said.
“This is just not just about hardening Kubernetes — it can be about how to make a protected application manufacturing facility,” he said. “It is about how to function Kubernetes, in a established of living paperwork that can improve as new technologies emerges.”
In addition to container and Kubernetes hardening for DevSecOps use, 1 of the sub-teams in the DoD undertaking will standardize a approach that generates steady authority to function for each application improve made by a govt agency.
It is a follow the Air Drive has by now executed under Chaillan, which indicates application modifications can be deployed swiftly to generation without the need of going as a result of a prolonged protection audit each and every time. Chaillan estimates this approach has minimize out 100 hours of deployment hold off for his group in the very last calendar year, and the group is ready to make various totally accredited application modifications for each working day.
