Transitioning to microservices has quite a few positive aspects for teams developing large apps, particularly those that ought to speed up the speed of innovation, deployments, and time to market place. Microservices also present know-how teams the option to protected their apps and solutions much better than they did with monolithic code bases.
Zero-believe in protection gives these teams with a scalable way to make protection idiot-proof whilst handling a growing variety of microservices and greater complexity. That’s proper. Even though it seems counterintuitive at initially, microservices permit us to protected our apps and all of their solutions much better than we ever did with monolithic code bases. Failure to seize that option will outcome in non-protected, exploitable, and non-compliant architectures that are only heading to turn out to be additional tough to protected in the long run.
Let us understand why we need zero-believe in protection in microservices. We will also critique a real-globe zero-believe in protection case in point by leveraging the Cloud Native Computing Foundation’s Kuma venture, a common support mesh designed on top of the Envoy proxy.
Safety just before microservices
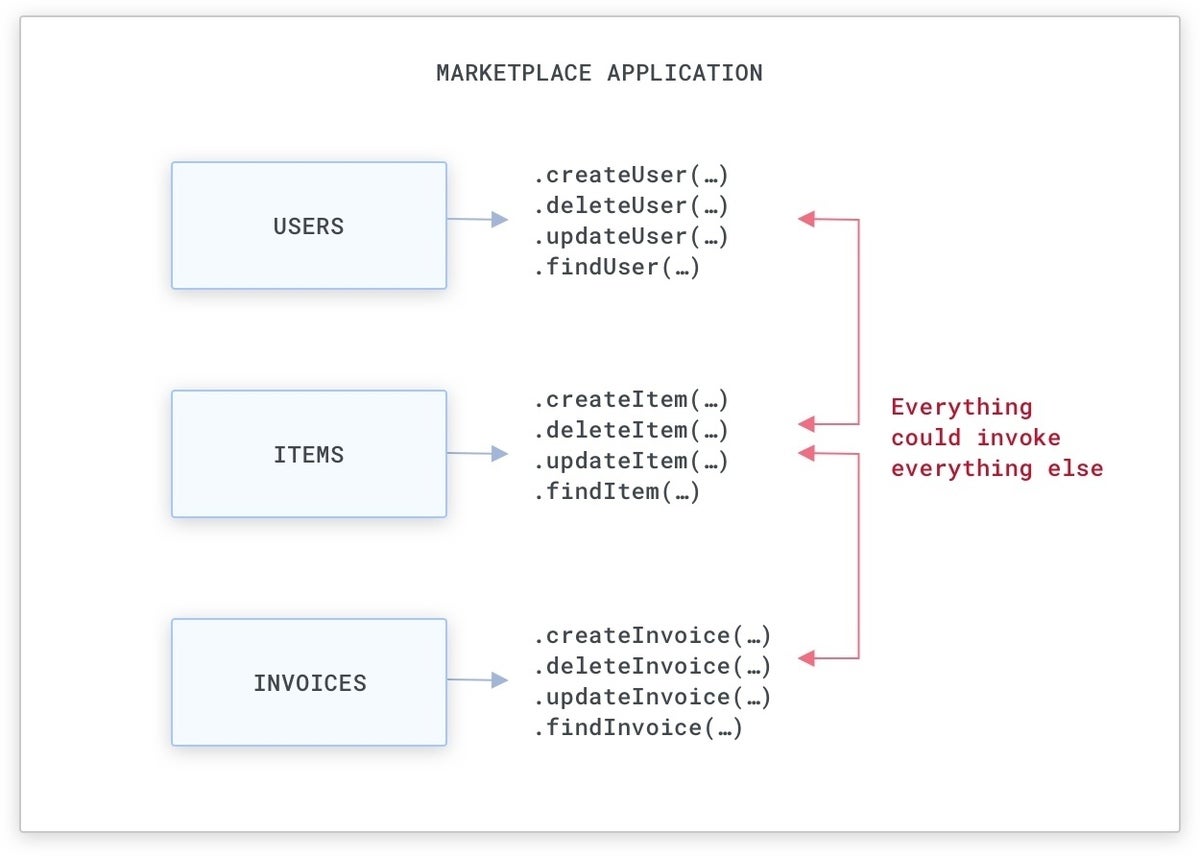
In a monolithic software, each and every resource that we produce can be accessed indiscriminately from each and every other resource by means of purpose phone calls since they are all aspect of the identical code foundation. Ordinarily, assets are heading to be encapsulated into objects (if we use OOP) that will expose initializers and features that we can invoke to interact with them and alter their condition.
For case in point, if we are developing a marketplace software (like Amazon.com), there will be assets that discover users and the products for sale, and that produce invoices when products are bought:
 Kong
KongA easy marketplace monolithic software.
Ordinarily, this suggests we will have objects that we can use to both produce, delete, or update these assets by means of purpose phone calls that can be utilised from everywhere in the monolithic code foundation. While there are ways to lessen access to sure objects and features (i.e., with public, private, and safeguarded access-level modifiers and bundle-level visibility), normally these procedures are not strictly enforced by teams, and our protection need to not depend on them.
 Kong
KongA monolithic code foundation is straightforward to exploit, since assets can be most likely accessed by everywhere in the code foundation.
Safety with microservices
With microservices, alternatively of owning each and every resource in the identical code foundation, we will have those assets decoupled and assigned to particular person solutions, with just about every support exposing an API that can be utilised by yet another support. As a substitute of executing a purpose call to access or alter the condition of a resource, we can execute a network request.
 Kong
KongWith microservices our assets can interact with just about every other by means of support requests in excess of the network as opposed to purpose phone calls in the identical monolithic code foundation. The APIs can be RPC-based, Rest, or anything else definitely.
By default, this doesn’t alter our problem: With no good obstacles in spot, each and every support could theoretically eat the uncovered APIs of yet another support to alter the condition of each and every resource. But since the communication medium has modified and it is now the network, we can use technologies and designs that operate on the network connectivity itself to established up our obstacles and identify the access degrees that each and every support need to have in the big image.
Knowledge zero-believe in protection
To carry out protection procedures in excess of the network connectivity among solutions, we need to established up permissions, and then check those permissions on each and every incoming request.
For case in point, we may perhaps want to permit the “Invoices” and “Users” solutions to eat just about every other (an bill is usually connected with a consumer, and a consumer can have quite a few invoices), but only permit the “Invoices” support to eat the “Items” support (because an bill is usually connected to an item), like in the pursuing scenario:
 Kong
KongA graphical illustration of connectivity permissions concerning solutions. The arrows and their route identify irrespective of whether solutions can make requests (eco-friendly) or not (pink). For case in point, the Items support can not eat any other support, but it can be consumed by the Invoices support.
Right after location up permissions (we will explore shortly how a support mesh can be utilised to do this), we then need to check them. The ingredient that will check our permissions will have to identify if the incoming requests are getting despatched by a support that has been authorized to eat the latest support. We will carry out a check someplace along the execution route, something like this:
if (incoming_support == “items”)
deny()
else
permit()
This check can be performed by our solutions them selves or by anything else on the execution route of the requests, but finally it has to take place someplace.
The most important trouble to address just before imposing these permissions is owning a reliable way to assign an id to just about every support so that when we discover the solutions in our checks, they are who they declare to be.
Id is crucial. With no id, there is no protection. When we travel and enter a new state, we demonstrate a passport that associates our persona with the document, and by carrying out so, we certify our id. Likewise, our solutions also ought to present a “virtual passport” that validates their identities.
Since the concept of believe in is exploitable, we ought to remove all kinds of believe in from our systems—and as a result, we ought to carry out “zero-trust” protection.
 Kong
KongThe id of the caller is despatched on each and every request by means of mTLS.
In purchase for zero-believe in to be executed, we ought to assign an id to each and every support instance that will be utilised for each and every outgoing request. The id will act as the “virtual passport” for that request, confirming that the originating support is certainly who they declare to be. mTLS (Mutual transportation Layer Safety) can be adopted to present each identities and encryption on the transportation layer. Since each and every request now gives an id that can be verified, we can then enforce the permissions checks.
The id of a support is typically assigned as a SAN (Topic Alternative Identify) of the originating TLS certification connected with the request, as in the circumstance of zero-believe in protection enabled by a Kuma support mesh, which we will explore shortly.
SAN is an extension to X.509 (a typical that is getting utilised to produce public vital certificates) that enables us to assign a customized value to a certification. In the circumstance of zero-believe in, the support title will be 1 of those values that is passed along with the certification in a SAN area. When a request is getting acquired by a support, we can then extract the SAN from the TLS certificate—and the support title from it, which is the id of the service—and then carry out the authorization checks knowing that the originating support definitely is who it promises to be.
 Kong
KongThe SAN (Topic Alternative Identify) is extremely frequently utilised in TLS certificates and can also be explored by our browser. In the image above, we can see some of the SAN values belonging to the TLS certification for Google.com.
Now that we have explored the importance of owning identities for our solutions and we understand how we can leverage mTLS as the “virtual passport” that is included in each and every request our solutions make, we are nevertheless still left with quite a few open subjects that we need to handle:
- Assigning TLS certificates and identities on each and every instance of each and every support.
- Validating the identities and checking permissions on each and every request.
- Rotating certificates in excess of time to increase protection and avoid impersonation.
These are extremely really hard difficulties to address since they properly present the backbone of our zero-believe in protection implementation. If not performed correctly, our zero-believe in protection product will be flawed, and as a result insecure.
Furthermore, the above duties ought to be executed for each and every instance of each and every support that our software teams are building. In a usual group, these support scenarios will incorporate each containerized and VM-based workloads managing throughout 1 or additional cloud suppliers, probably even in our physical datacenter.
The most important error any group could make is inquiring its teams to develop these functions from scratch each and every time they produce a new software. The ensuing fragmentation in the protection implementations will produce unreliability in how the protection product is executed, building the entire technique insecure.
Service mesh to the rescue
Service mesh is a sample that implements modern-day support connectivity functionalities in such a way that does not have to have us to update our apps to choose advantage of them. Service mesh is typically delivered by deploying info aircraft proxies following to each and every instance (or Pod) of our solutions and a control aircraft that is the source of reality for configuring those info aircraft proxies.
 Kong
KongIn a support mesh, all the outgoing and incoming requests are instantly intercepted by the info aircraft proxies (Envoy) that are deployed following to just about every instance of just about every support. The control aircraft (Kuma) is in charge of propagating the guidelines we want to established up (like zero-believe in) to the proxies. The control aircraft is never ever on the execution route of the support-to-support requests only the info aircraft proxies live on the execution route.
The support mesh sample is based on the concept that our solutions need to not be in charge of handling the inbound or outbound connectivity. Above time, solutions created in diverse technologies will inevitably end up owning a variety of implementations. Thus, a fragmented way to regulate that connectivity finally will outcome in unreliability. Plus, the software teams need to focus on the software itself, not on handling connectivity because that need to preferably be provisioned by the fundamental infrastructure. For these good reasons, support mesh not only gives us all sorts of support connectivity operation out of the box, like zero-believe in protection, but also helps make the software teams additional effective whilst giving the infrastructure architects full control in excess of the connectivity that is getting produced in the group.
Just as we didn’t talk to our software teams to stroll into a physical info centre and manually hook up the networking cables to a router/swap for L1-L3 connectivity, today we never want them to develop their very own network management software for L4-L7 connectivity. As a substitute, we want to use designs like support mesh to present that to them out of the box.
Zero-believe in protection by means of Kuma
Kuma is an open source support mesh (initially designed by Kong and then donated to the CNCF) that supports multi-cluster, multi-area, and multi-cloud deployments throughout each Kuberenetes and digital machines (VMs). Kuma gives additional than 10 guidelines that we can implement to support connectivity (like zero-believe in, routing, fault injection, discovery, multi-mesh, and many others.) and has been engineered to scale in large distributed business deployments. Kuma natively supports the Envoy proxy as its info aircraft proxy know-how. Ease of use has been a focus of the venture because day 1.
 Kong
KongKuma can run a distributed support mesh throughout clouds and clusters — which includes hybrid Kubernetes in addition VMs — by means of its multi-zone deployment method.
With Kuma, we can deploy a support mesh that can deliver zero-believe in protection throughout each containerized and VM workloads in a solitary or multiple cluster setup. To do so, we need to adhere to these steps:
one. Download and set up Kuma at kuma.io/set up.
two. Start off our solutions and get started `kuma-dp` following to them (in Kubernetes, `kuma-dp` is instantly injected). We can adhere to the receiving began recommendations on the installation web site to do this for each Kubernetes and VMs.
Then, at the time our control aircraft is managing and the info aircraft proxies are productively connecting to it from just about every instance of our solutions, we can execute the closing stage:
3. Empower the mTLS and Targeted traffic Permission guidelines on our support mesh by means of the Mesh and TrafficPermission Kuma assets.
In Kuma, we can produce multiple isolated digital meshes on top of the identical deployment of support mesh, which is typically utilised to guidance multiple apps and teams on the identical support mesh infrastructure. To enable zero-believe in protection, we initially need to enable mTLS on the Mesh resource of decision by enabling the mtls property.
In Kuma, we can determine to permit the technique produce its very own certification authority (CA) for the Mesh or we can established our very own root certification and keys. The CA certification and vital will then be utilised to instantly provision a new TLS certification for each and every info aircraft proxy with an id, and it will also instantly rotate those certificates with a configurable interval of time. In Kong Mesh, we can also discuss to a third-social gathering PKI (like HashiCorp Vault) to provision a CA in Kuma.
For case in point, on Kubernetes, we can enable a builtin certification authority on the default mesh by implementing the pursuing resource by means of kubectl (on VMs, we can use Kuma’s CLI kumactl):
apiVersion: kuma.io/v1alpha1
kind: Mesh
metadata:
title: default
spec:
mtls:
enabledBackend: ca-one
backends:
- title: ca-one
variety: builtin
dpCert:
rotation:
expiration: 1d
conf:
caCert:
RSAbits: 2048
expiration: 10y
