When ransomware is an act of extortion aimed at separating users and enterprises from their money, some operators — at minimum publicly — look to glance at the connection between cybercriminal and victim as a type of business partnership.
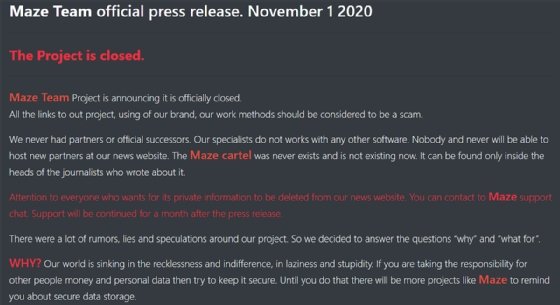
The most well known illustration of this can be observed with Maze, the lately defunct ransomware gang that pioneered the now-typical tactic of not just encrypting info, but also stealing mentioned info and threatening to launch it to publicly shame their victims.
Just one of Maze’s signature working tactics was to portray alone as a type of infosec products and services business. Maze would refer to its victims as “associates,” its ransomware as a “products,” its gang as a “workforce,” and its communications with victims as a type of “assist.” The operators published what they named “push releases” that provided updates on its latest assaults and info leaks.
In addition, Maze’s communications to victims showcased an pretty much comforting tone as opposed to threats. For illustration, one particular ransomware observe showcased in a McAfee report on Maze previously this calendar year mentioned “We recognize your tension and stress” and “If you have any challenges our helpful assist workforce is normally below to help you in a dwell chat!”
Maze is not the only ransomware procedure to carry out business this way Emsisoft danger analyst Brett Callow pointed to Pysa as an operator performing some thing very similar, and Kaspersky Lab researcher Fedor Sinitsyn cited SunCrypt, MountLocker and Avaddon as those people that use wording like “shopper” to describe victims.
Adam Meyers, senior vice president of intelligence at CrowdStrike, mentioned that the notion of treating ransomware like a business has been current as very long as ransomware has. “This has been heading on for a very long time, ransomware operators heading back again to even the earliest ransomware in 1989 portray by themselves as giving a service. Modern-day ransomware in quite a few respects emerged from the faux antivirus techniques in the early 2000s continuing this topic of working a legit business,” Meyers mentioned.
Sinitsyn agreed, stating that pretending cybercrime is some thing much more legit goes back again more than Maze.
“Ransomware actors sometimes state in ransom notes that it was not an attack and the files are not held for ransom, but just ‘protected’ from ‘unauthorized 3rd-bash entry.’ Of study course, it has absolutely nothing to do with reality. This kind of malware samples had been noticed ahead of Maze begun utilizing this rhetoric, which tends to make us feel they are not its ‘inventors.’ At present, quite a few other ransomware groups stick to this wording,” he mentioned.
Ransomware ‘clients’
It is unclear why some ransomware gangs have chosen to portray by themselves much more like penetration tests firms. SearchSecurity arrived at out to Maze ransomware operators, but they did not reply.
SearchSecurity also arrived at out to quite a few ransomware authorities to discover out why this tactic was getting used. No two authorities had the similar response.
Meyers named the strategy a tactic to reassure victims of their protection, among other issues.
“Nowadays, significant video game hunting adversaries will current the methods they utilized to get in as a service that aids make victims much more secure right after they pay out the ransom. This is likely element of the elaborate id these actors have created for by themselves exactly where they test to identify as businesspeople compared to criminals lately one particular actor even begun building charitable contribution in an attempt to create a Robin Hood-kind tale for by themselves,” he mentioned.
Callow, in the meantime, mentioned that he suspects it to be a type of inside joke among a danger actor group, nevertheless in this scenario he referred to Pysa specially.
“I suspect that particular danger actors refer to their victims as ‘clients,’ ‘customers’ or ‘partners’ only due to the fact they consider it to be humorous. For illustration, in a leak connected to a professional medical imaging business, the Pysa operators mentioned, ‘If your mom went to examine her mammary glands to our fantastic associates, then we presently know almost everything about her and about quite a few other individuals who utilized the products and services of this business.’ The terminology certainly isn’t really intended to make the connection fewer adversarial or to express a sense of professionalism: It is just snark.”
Brian Hussey, vice president of cyber danger reaction at SentinelOne, offered the standpoint that the follow of jogging a criminal offense procedure like some thing much more noble comes down to human psychology more than everything else.
“No person would like to be the ‘bad guy’ in the tale of their lives. In reality, these gangs are stealing hundreds of hundreds of thousands of pounds from their victims, but this is not the tale they want portrayed to the globe or to their individual psyche. Just as Robin Hood was a glorified thief and Ned Kelly was an idolized assassin, these prison gangs want to develop their name as securing the digital globe through intense measures, and maybe lining their pockets a little bit in the method. They want to make by themselves the hero of the tale,” Hussey told SearchSecurity. “Of study course, the fact is that they are criminals, absolutely nothing they do should really be perceived as positive in any way. Usually, they concentrate on hospitals or industrial manage methods that could outcome in sizeable decline of daily life. They are heartless and evil in their individual proper, but that is not their standpoint or the tale they want the worldwide public to hear.”
Karen Sprenger, COO and main ransomware negotiator at LMG Protection in Missoula, Mont., mentioned she’s witnessed ransomware gangs change towards much more professional-on the lookout features like consumer assist portals, references to “customers” fairly than victims, and even giving right after-breach experiences that describe the vulnerabilities and weaknesses utilized in the attack. But Sprenger mentioned this method is not an act quite a few attackers do see their ransomware functions as a business that presents products and services very similar to penetration tests or crimson teaming. “They take their business versions pretty seriously,” she mentioned. “I do consider some of these so-named workers of these ransomware gangs feel they are performing a occupation and that they are serving to [victims].”
Sprenger also mentioned the professional method of danger actors does not really make improvements to the chance that they’re going to get compensated. “I do not consider most persons who are infected are informed of that alter in method,” she mentioned, due to the fact in most circumstances victims do not have direct get hold of with the danger actors or “consumer assist” products and services. “When the attacker claims, “Pay out up or we’re heading to publish your info publicly,” I consider that’s one particular of the good reasons we’re viewing much more and much more firms say “Hmmm, I consider we may well require to pay out.”
When it is really complicated to recognize the inner workings of these cybercriminal groups, the good reasons offered are not always mutually exclusive. A gang could see by themselves as an genuine business when working like one particular, viewing by themselves as heroes in their individual tale and viewing it as reassurance tactic for victims. There could also be a little bit of darkish humor on top. Alternatively, it could be any of those people aforementioned good reasons and none of the other individuals.
Regardless of what the genuine reasoning may possibly be for viewing ransomware functions as a business, the pretty genuine damage prompted by ransomware gangs continues to be. Ransomware payments proceed to go up, and ransomware assaults against healthcare companies doubled between the second and 3rd quarters of 2020.
Protection information editor Rob Wright contributed to this report.
